Difference between revisions of "Dashboard Technical Specifications -- SaaS"
(No difference)
|
Revision as of 11:51, 5 May 2013
Contents
Introduction
The Dolcera Dashboard is a web application for managing and organizing patents, product information, and scientific literature. This application is used for a variety of purposes including patent review/clearance, and by different enterprise users including attorneys, licensing professionals, engineers, and executives.
Use Cases
The typical use cases for the Dolcera Dashboard are as follows:
- Freedom-to-practice or clearance search
- Patent portfolio analysis
- Competitive intelligence
- Patent landscaping
- Patent-to-product mapping
- Patent-to-standard mapping
User Communities
The typical users of the Dolcera Dashboard include:
- Patent attorneys
- Patent managers
- Patent searchers
- Engineers, scientists and inventors
- Licensing and business development professionals
- Senior executives
What is the Dolcera Dashboard?
The Dolcera Dashboard is an interactive web application used to:
- Organize large quantities of patent, scientific and product literature
- Manage patent review workflows
- Assist in collaboration with colleagues and partners around the world
- Help technology teams, patent counsels, and key decision makers in monitoring the competitive landscaping and finding key partners
Workflow
A typical workflow is described below:
- Log into the system
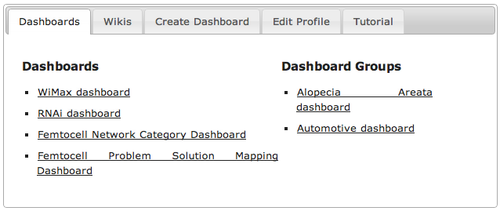
- Select the dashboard (workfile)
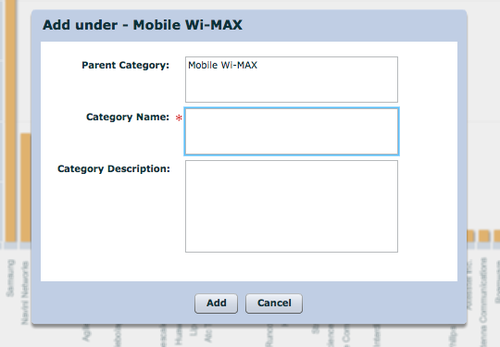
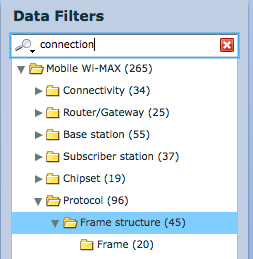
- Create categories (taxonomy)
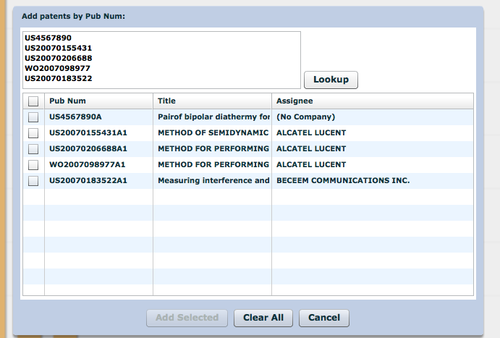
- Add patents
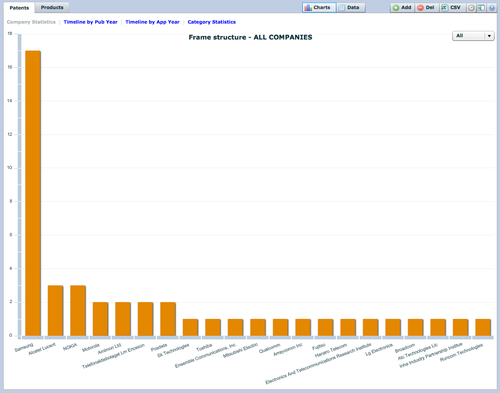
- Review charts
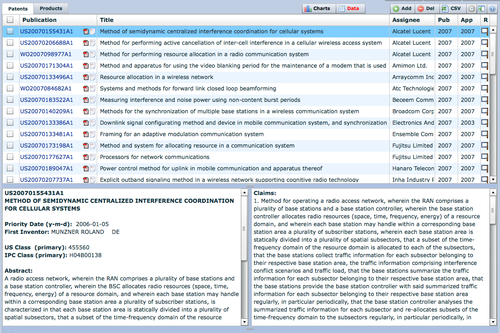
- Review patents
- Search patents
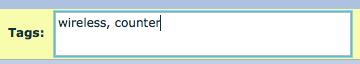
- Tag patents
- Add review notes for patents
- Export patents and analysis
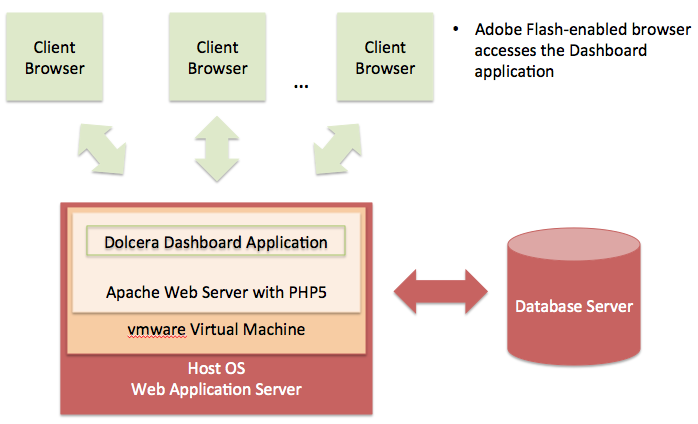
Deployment Architecture
Software-as-a-Service (SaaS) Environment
The Dolcera Dashboard service is made available as an online service (SaaS) to the users. The users log into the application through their web browser, and can use the application online.
Security Controls
Dolcera has extensive security controls in place to protect client confidential information and to share the results of Dolcera's research and analysis in a secure manner with our clients.
The Dolcera IT team has implemented secure procedures at its facilities in the US and India, and at its data centers in the US.
Authentication and Authorization
- All access to client-specific information is obtained after authentication via a username and password
- Client users who require access to data and systems at Dolcera must be authorized by the Dolcera account management team in consultation with the appropriate client management.
- Only those Dolcera team members who are directly involved with a particular client are authorized to access client-related data.
- Dolcera regularly reviews and updates the authorizations of team members as appropriate, based on their work assignments.
- Infrastructure logs and audit trails contain information about security-related events including logins, IP address, date and time of access.
Physical Security
- Dolcera's India facility is protected by a 24 hour security guard.
- US data center facilities are protected by the highest level of physical and biometric access controls.
Redundancy
- Dolcera systems have several levels of redundancy, including multiple servers, multiple storage and backup solutions, multiple network connections and multiple levels of physical and data security.
Data Backups
- Data is backed up on a nightly basis or in real time as appropriate, and is securely synchronized to the Dolcera servers located in the US data center.
Intrusion Detection
- Intrusion detection systems have been installed on Dolcera servers and are monitored by the Dolcera team.
Disaster Recovery
- Dolcera has a disaster recovery plan and the necessary technology and systems (including data backups and alternative designated work sites) to implement the disaster recovery procedures in case of need.